Trust computer for delegation option
And yet Kerberos keeps getting documentation. This ongoing need to clarify how Kerberos works and how it fails is a result of the fact that—although Kerberos remains the same—the services that use it and the ways they use it are often unique. This is important because if you know what the different settings that can be configured in AD for a service do, you can make sense out of what settings you might need for an application or service that uses Kerberos delegation.
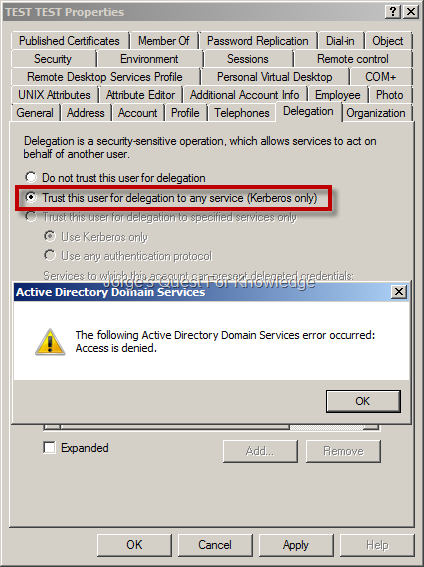
Figure 1 shows the tab in question. Delegation aka impersonation or simple delegation is the act of an application or service getting Kerberos tickets to gain access to resources on a remote computer on behalf of a user. The identity that is trusted for that delegation is the service account that the application is running as.
This allows the application to gain access only to resources the user would have access to and to provide that information back to the user. A typical scenario would be a web server connecting to a SQL Server system to display data to a user on a web client. The top two settings in Figure 2 are self-explanatory. The third is essentially Constrained Delegation KCD , which is like simple delegation but guarantees that the identity being impersonated will be impersonated only to specific services on specific computers.
This setting is a security enhancement because where and how a user can be impersonated is limited, so that if a service identity which is being trusted for delegation is ever compromised the effect is limited to being able to access only those specific resources on the remote servers that are manually selected for constrained delegation. The fourth setting in Figure 2 allows KCD as well as Services for User.
S4U allows for more advanced functions—such as protocol transition—and is actually pretty complex. What is protocol transition?
It occurs when a client authenticates with a protocol other than Kerberos incoming to the computer and then is transitioned to Kerberos. LDP is a tool installed with the AD Domain Services role, by default, which can be used as a GUI-based LDAP-querying tool.
LDP is basically a tool to let you construct your own LDAP queries and see the results in a relatively nice, friendly interface. The added value in using LDP to look at values such as userAccountControl is that LDP will interpret computed flag values into human-readable results instead of leaving them as a combination of numerical values.
To be fair, later versions of adsiedit. In other words, in Windows Server and later, ldp. Do not trust for delegation. Figure 4 shows an account that is trusted for delegation.
This flag is what allows simple, unconstrained Kerberos delegation to take place for that service identity. Trusted for delegation to specified services.
These entries are the specific services on the specific computer that delegation will be allowed to. The second option here is the less secure Use any authentication protocol radio button, which allows for protocol transition and other advanced uses.
Without the T2A4D flag being present, you can expect protocol transition to fail. Note that this simple radio button is extremely important because without it selected, S4U2Self, S4U2Proxy, and protocol transition will behave differently and can cause problems for applications and services that use expect these kinds of tickets.
In the case of protocol transition, it will fail. No ticket will be issued. For S4U2Proxy and S4U2Self, they will fail to have the forwardable flag present, which also results in a failure in every case for S4U2Proxy and in situations where S4U2Self needs to send a ticket to another service or host.
What happens if the service account that an application or service is running as must do an action that requires protocol transition, and the Delegation tab is configured for Use Kerberos only and not Use any authentication protocol? The ambiguity of how the failure would appear accents some of the pain of this kind of problem.
However, the most likely result would be an Access Denied error message. In this situation, be sure to check the application or service documentation to see if they state that protocol transition or TGT-less service ticket requests will take place. Once you have that capture, filter it for Kerberos Kerberosv5 in Microsoft Network Monitor or kerberos in Wireshark.
More information about how the Microsoft Kerberos implementation works can be found in the online Open Protocol specification. Hopefully, this breakdown of what the UI settings for Kerberos are and what they correspond to in AD helps make sense of things. Knowing what should be present when things are working is half the battle.
Windows Server Deep Dive with John Savill June How to Secure your Endpoints: Do it Right, Keep it Right June Capacity Planning Done Right for SQL Server June Building Intelligent Applications with Azure Machine Learning with Stefano Tempesta June Operational Excellence In Managing Your SQL Server Infrastructure with Victor Isakov June Windows 10 Creators Update — Overview, Customization, Security and Privacy with Richard Hay July Overcoming the Biggest Data Center Challenges When Working with Colocation July Planning your Azure migration and deployment projects with Peter de Tender July Eliminating the Risk in Migrating Active Directory July To submit an article, please log in and then click Contribute.

If you are not a registered user on Windows IT Pro, click Register. Learn more about contributing to IT Pro. Get answers to questions, share tips, and engage with the IT professional community at myITforum.
What is this option Trust computer for delegation?
Are you a data center professional? Looking to get things done in web development? Hot Scripts offers tens of thousands of scripts you can use.
() Delegating The Configuration Of "Trusted For Delegation" In AD « Jorge's Quest For Knowledge!
Skip to Navigation Skip to Content. Display name or email address: The Most Confusing Dialog Box in Active Directory This breakdown of Kerberos settings and how they correspond to AD provides much-needed clarity. Apr 26, Tim Springston. Related Articles The Most Confusing Dialog Box in Active Directory 1 How can I use Group Policy to hide the domain drop down list on the Windows Logon dialog box? I installed Group Policy Management Console GPMC.
How can I undo the changes it makes to the Group Policy tab of my Site, Domain, and Organizational Unit OU Properties dialog boxes. Upcoming Training June You Contribute To submit an article, please log in and then click Contribute. Windows IT Pro Guest Blogs Veeam All Sponsored Blogs Learn more about contributing to IT Pro. Join the Conversation Get answers to questions, share tips, and engage with the IT professional community at myITforum. Site Features Contact Us Awards Community Sponsors Media Center RSS Sitemap Site Archive View Mobile Site.
Penton Privacy Policy Terms of Service.